Which Are The Most Secure Smartphones in 2017 - How to, Technology and PC Security Forum | SensorsTechForum.com

USB Kill Can Destroy Your Computer In Few Seconds - How to, Technology and PC Security Forum | SensorsTechForum.com

Which Are The Most Secure Smartphones in 2017 - How to, Technology and PC Security Forum | SensorsTechForum.com

Worm:VBS/Tibni.A and Bahaty.com/search/– Remove Them From Your PC - How to, Technology and PC Security Forum | SensorsTechForum.com
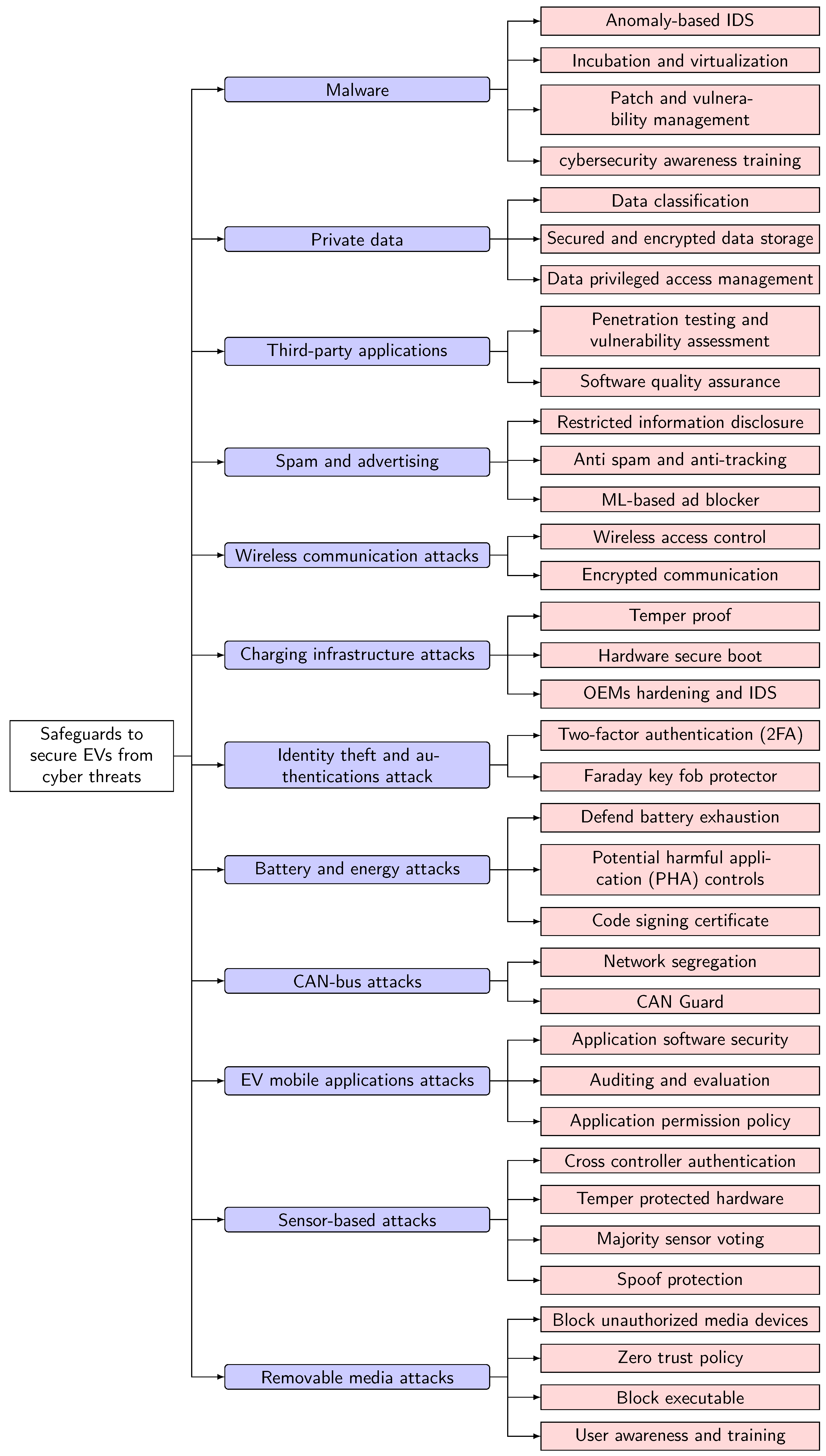
Energies | Free Full-Text | Emerging Cybersecurity and Privacy Threats to Electric Vehicles and Their Impact on Human and Environmental Sustainability