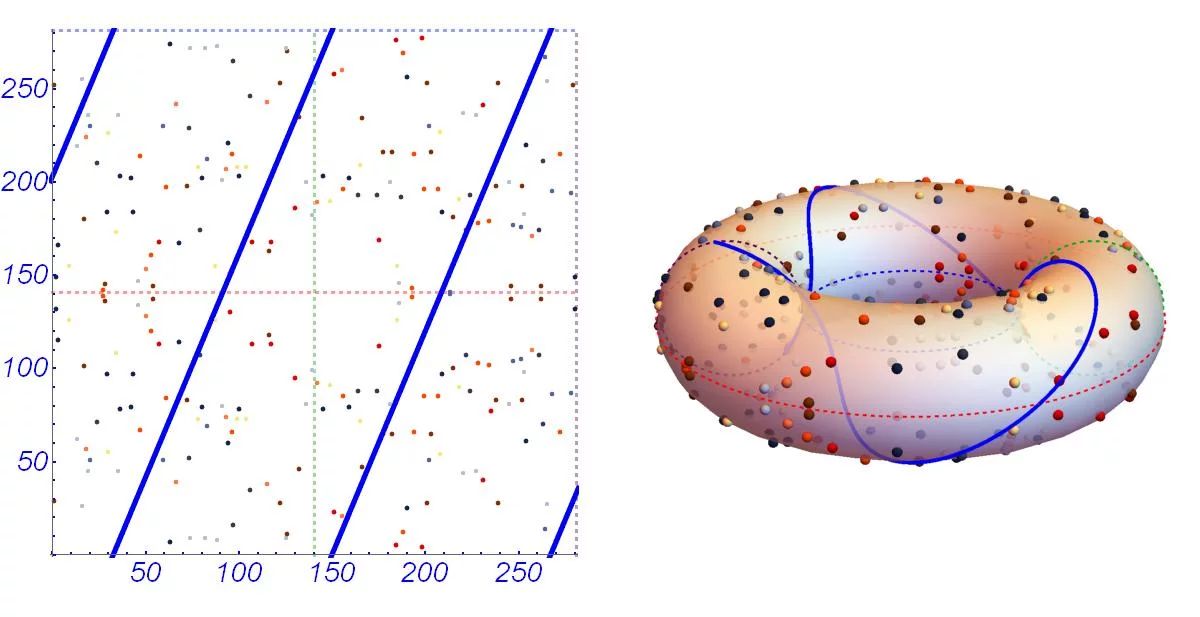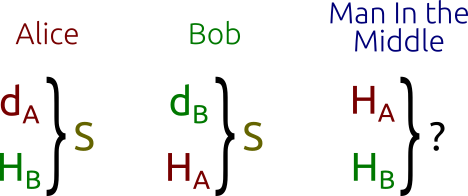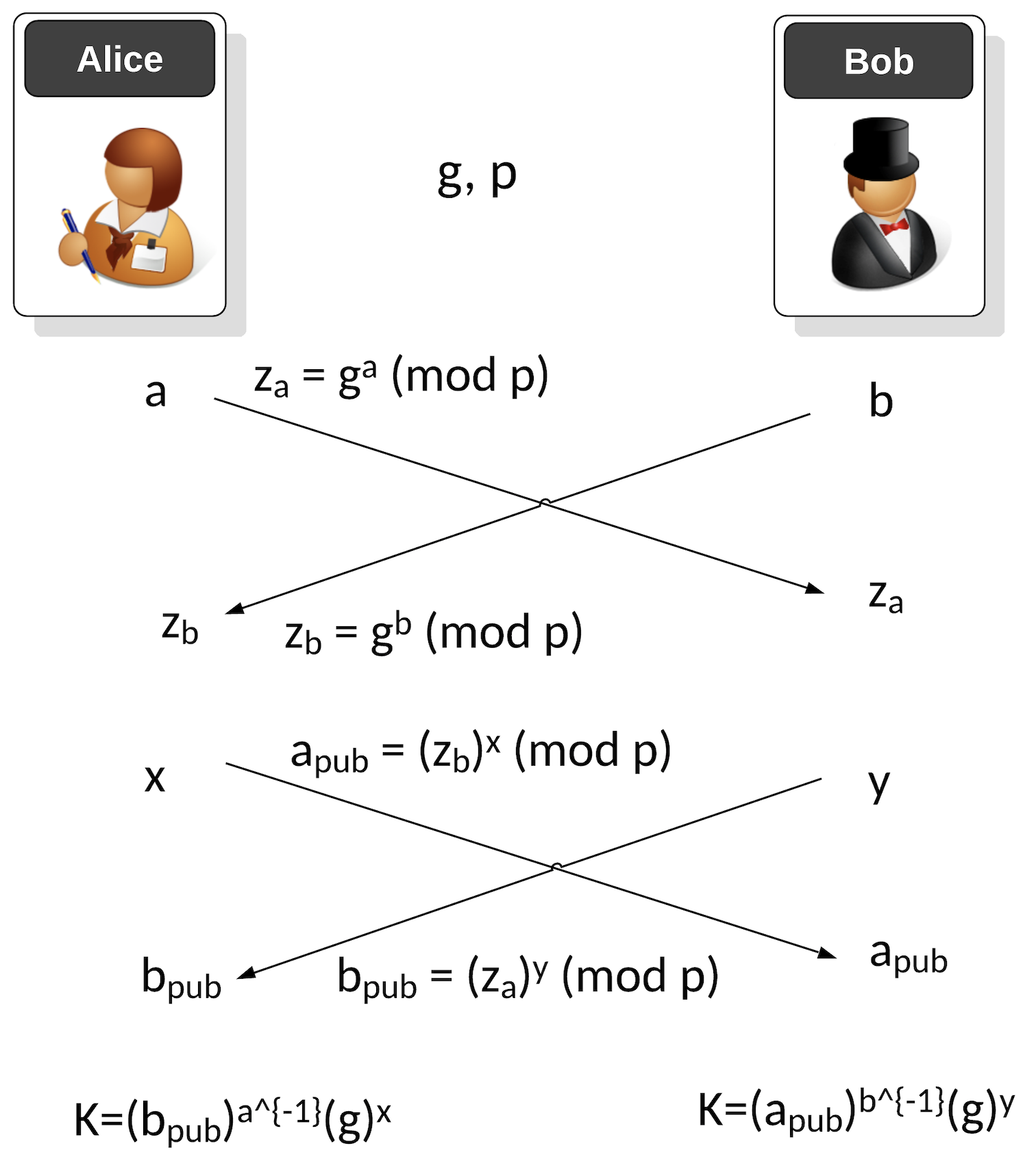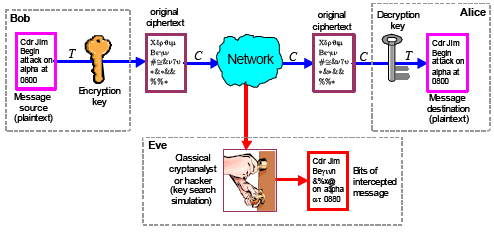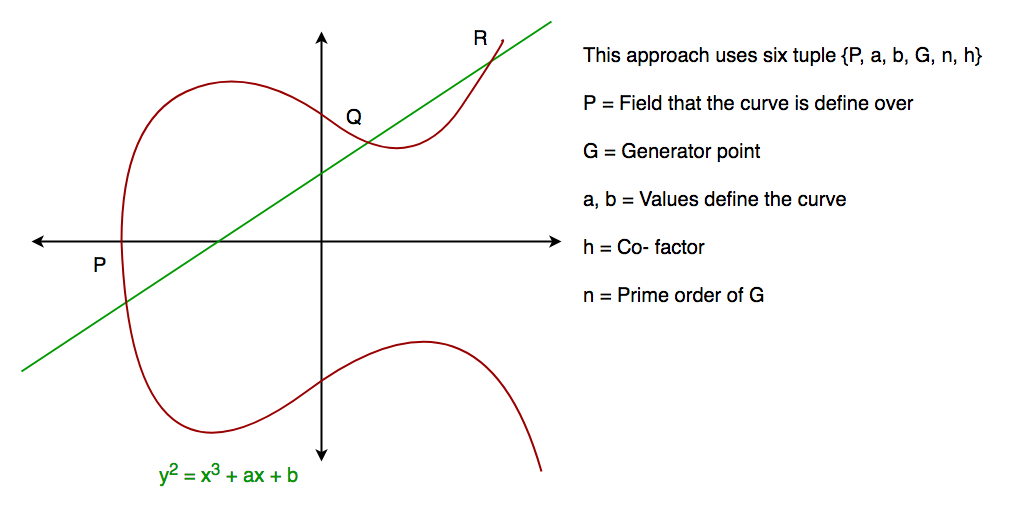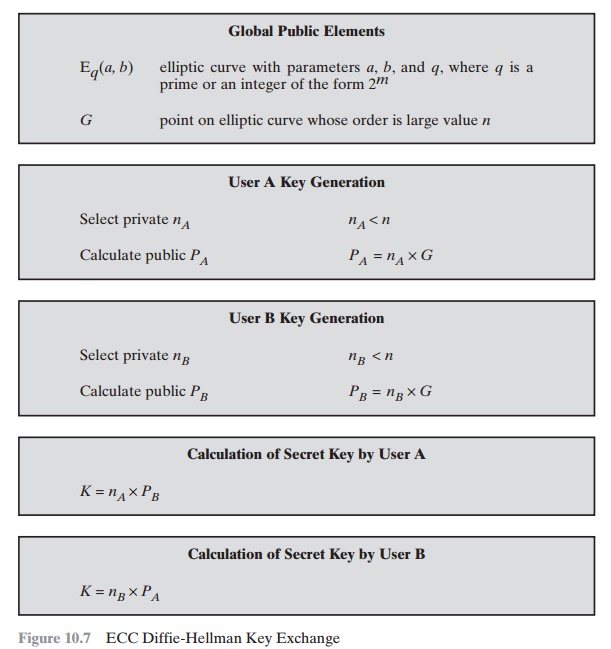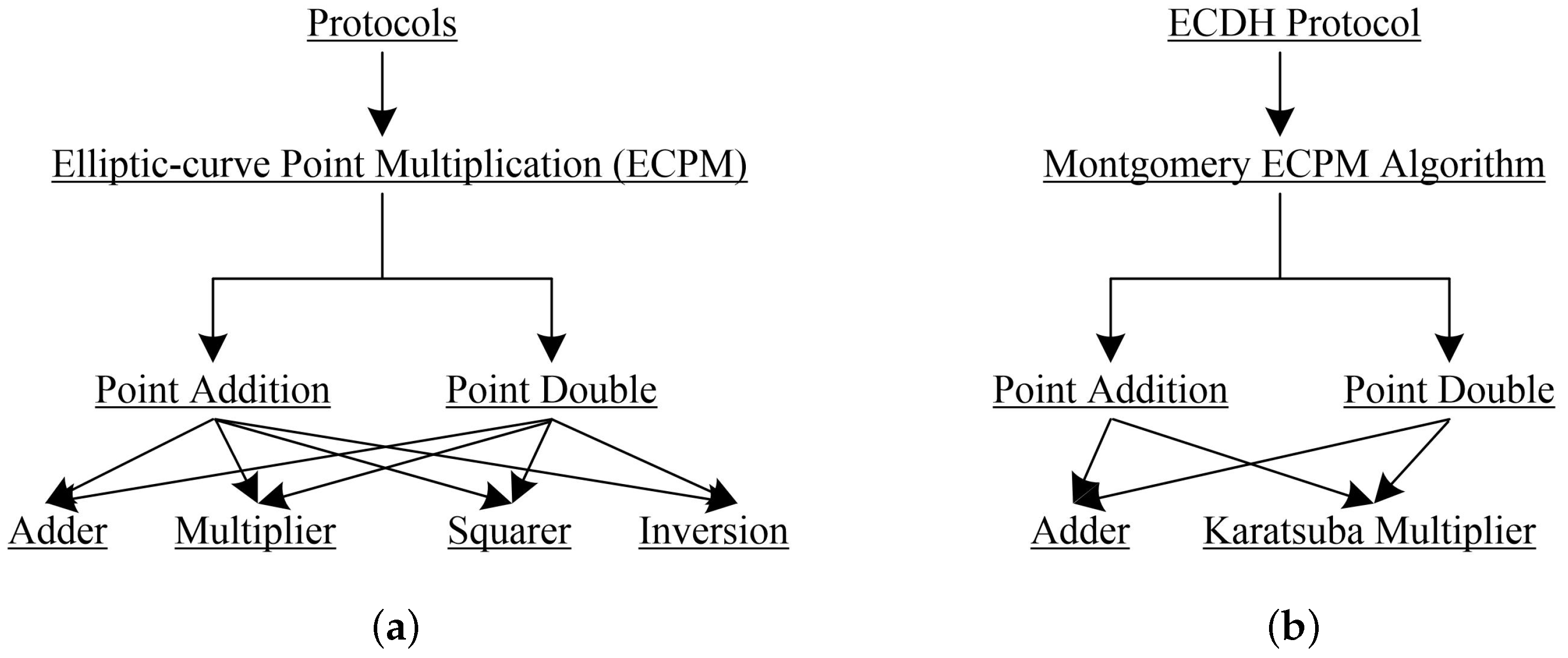
Applied Sciences | Free Full-Text | Throughput/Area Optimized Architecture for Elliptic-Curve Diffie-Hellman Protocol

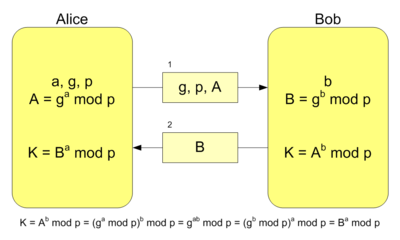
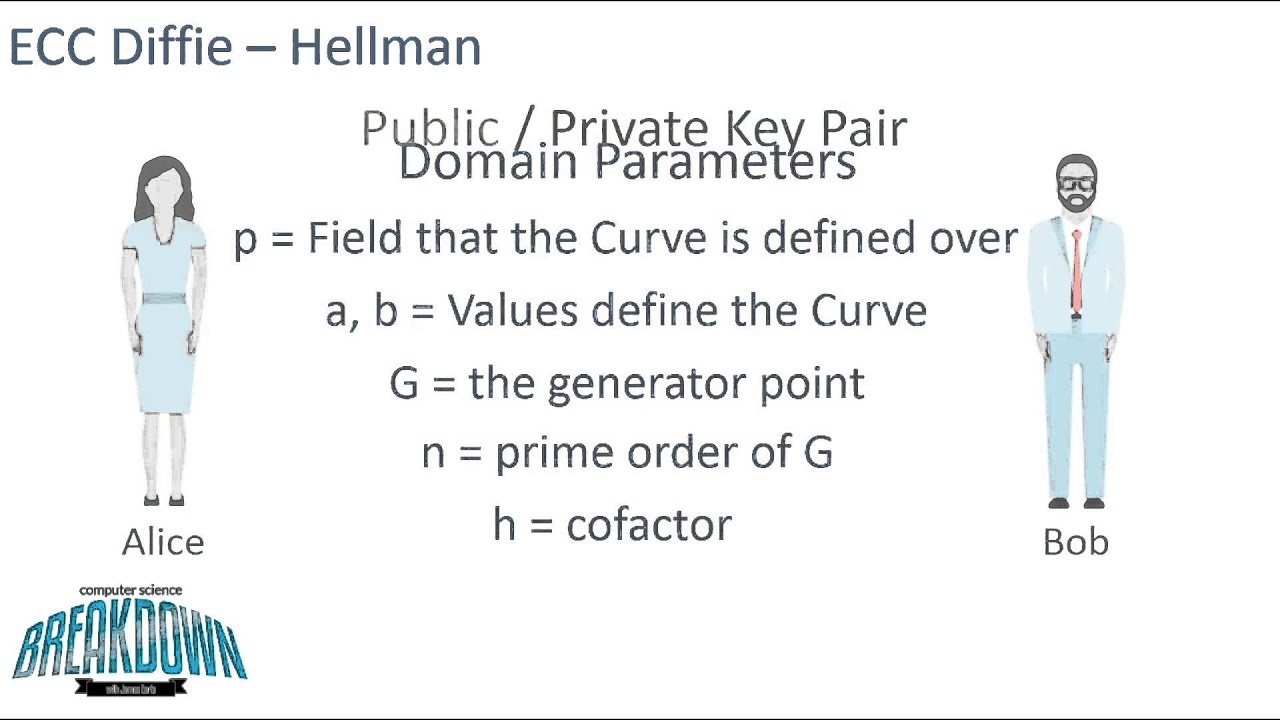
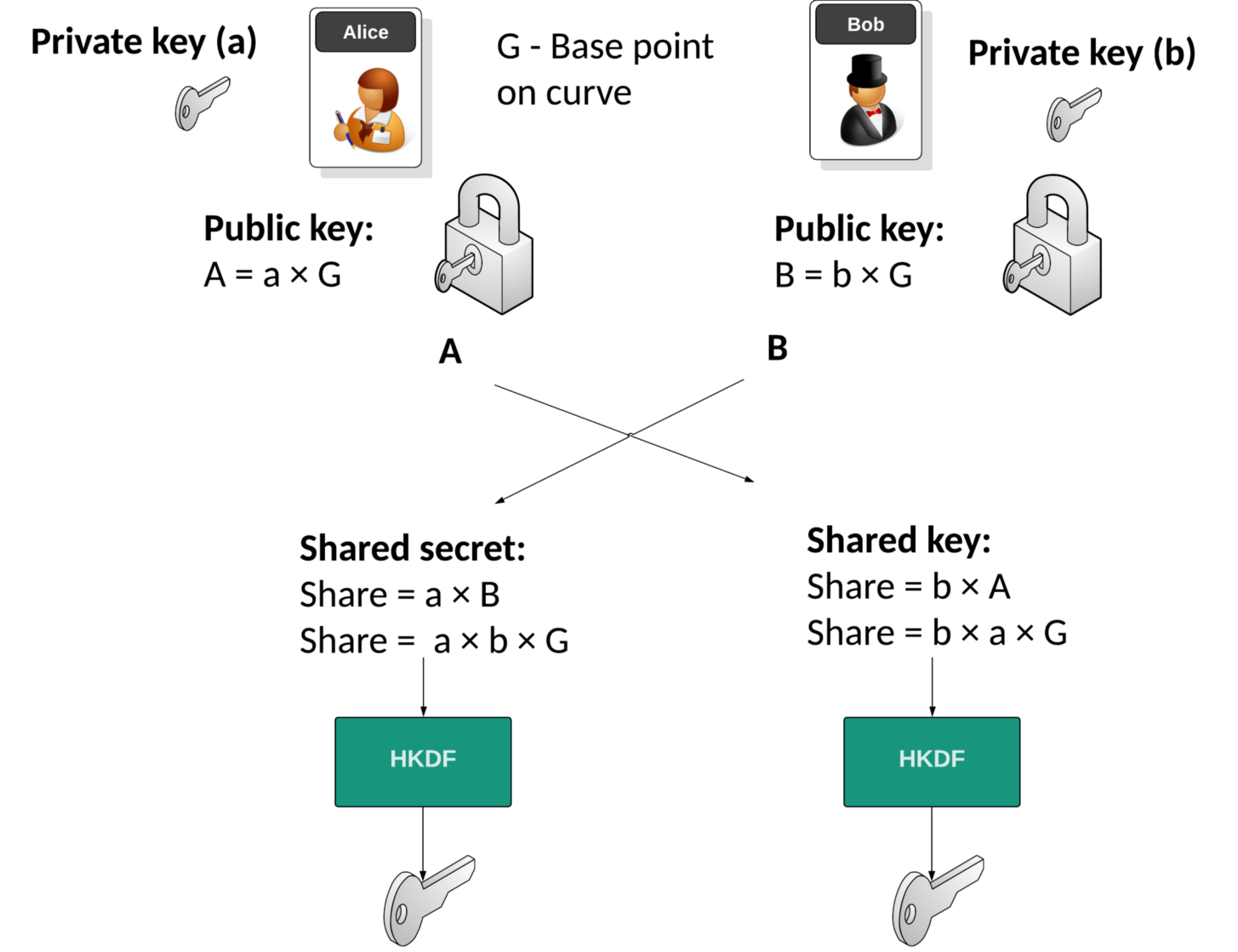
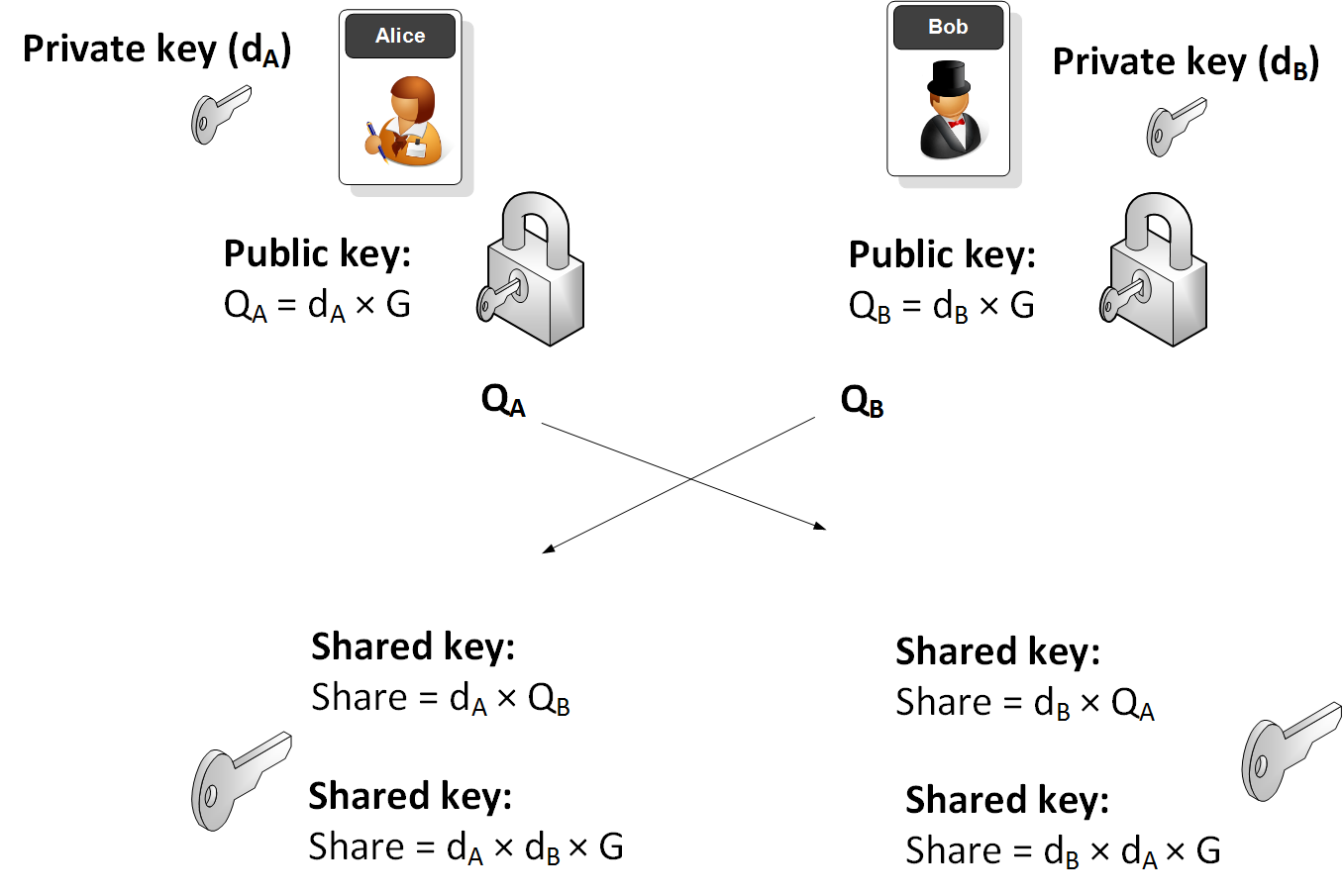
Keys to Understanding WPA3 – SAE : Diffie-Hellman Key Exchange, Elliptic Curve Cryptography and Dragonfly Key Exchange – Wireless Gnan
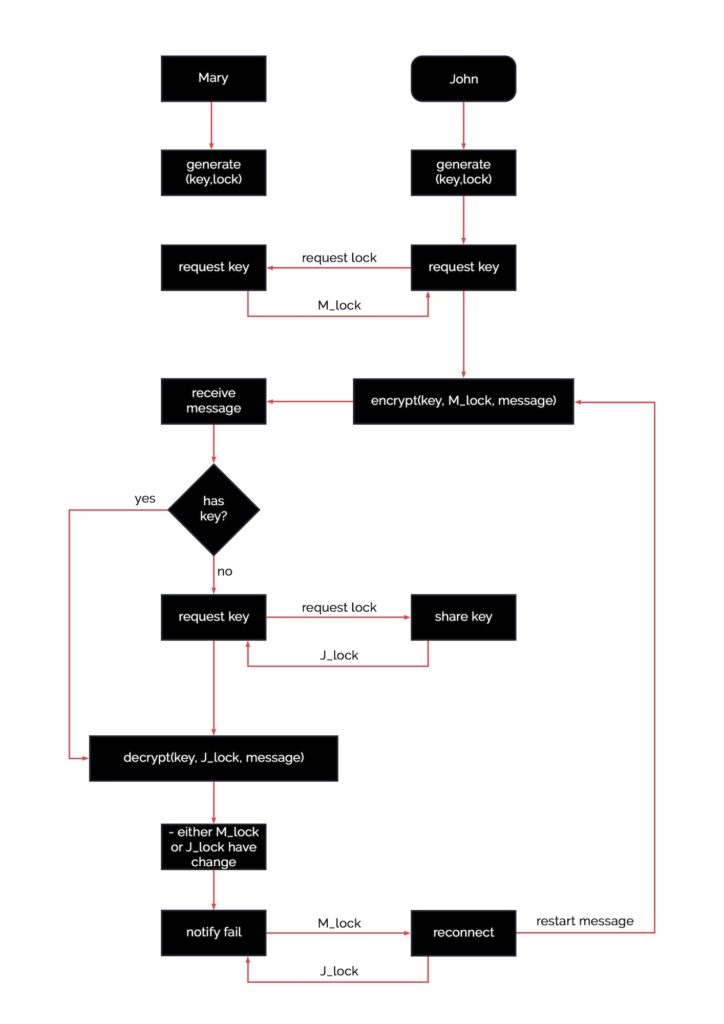
![PDF] Enhanced Elliptic Curve Diffie-Hellman Key Exchange Algorithm for Ornamental Security based on Signature and Authentication Algorithm | Semantic Scholar PDF] Enhanced Elliptic Curve Diffie-Hellman Key Exchange Algorithm for Ornamental Security based on Signature and Authentication Algorithm | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/82bcce2f2beac5abf74e0901fe9535264050459a/4-Figure4-1.png)